- This topic is empty.
-
AuthorPosts
-
-
March 6, 2025 at 3:15 am #7413
Kris Marker
Keymaster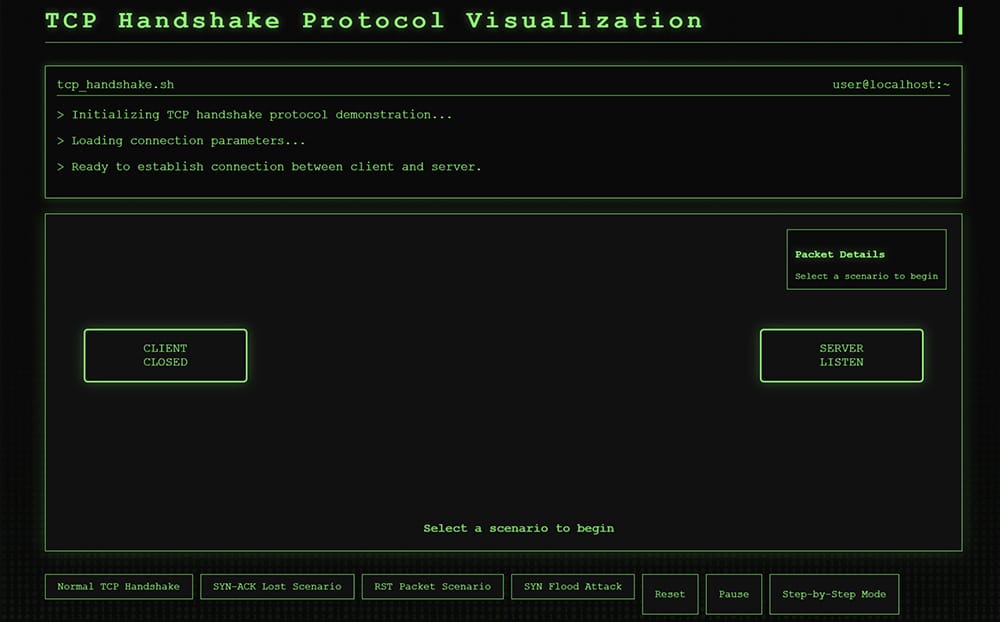
🔐 NEW PROJECT: TCP Handshake Interactive Visualization 🔐
Excited to share my latest open-source educational tool: an interactive visualization of the TCP three-way handshake process!
This browser-based tool demonstrates:
- The standard SYN → SYN-ACK → ACK handshake
- Packet loss recovery scenarios
- RST packet connection rejections
- SYN flood DDoS attack simulations
Built with D3.js and vanilla JavaScript, it features a terminal-inspired interface with color-coded packet animations, making it perfect for cybersecurity education and network protocol training.
All code is available on GitHub under MIT license. No installation required – just clone and open in any modern browser.
Check it out: https://github.com/DoingFedTime/TCP-Handshake-Explained-Interactive
TCP Handshake Visualization
TCP Handshake Protocol Visualization
tcp_handshake.sh
user@localhost:~> Initializing TCP handshake protocol demonstration…
> Loading connection parameters…
> Ready to establish connection between client and server.
CLIENTCLOSEDSERVERLISTENPacket Details
Select a scenario to beginSelect a scenario to begin
Understanding the TCP Handshake
The TCP handshake is a three-way process used to establish a reliable connection between two devices before data is exchanged:
1. SYN (Synchronize)
The client sends a SYN packet to the server, indicating it wants to establish a connection. This packet contains an initial sequence number (ISN) that will be used to track bytes in the stream.
2. SYN-ACK (Synchronize-Acknowledge)
The server responds with a SYN-ACK packet. This acknowledges the client’s SYN packet (by incrementing the client’s sequence number by 1) and includes the server’s own sequence number.
3. ACK (Acknowledge)
The client acknowledges the server’s response by sending an ACK packet, which increments the server’s sequence number by 1. After this step, a full-duplex connection is established.
Connection States
During the handshake, the TCP connection transitions through several states:
- CLOSED: No connection
- LISTEN: Server waiting for connections
- SYN-SENT: Client has sent SYN, waiting for SYN-ACK
- SYN-RECEIVED: Server has received SYN, sent SYN-ACK
- ESTABLISHED: Connection established, data transfer can begin
TCP Handshake in Code
Socket Programming Example (C)
// Server-side code #include <stdio.h> #include <stdlib.h> #include <string.h> #include <unistd.h> #include <sys/socket.h> #include <netinet/in.h> int main() { int server_fd, new_socket; struct sockaddr_in address; int addrlen = sizeof(address); // Creating socket if ((server_fd = socket(AF_INET, SOCK_STREAM, 0)) == 0) { perror("socket failed"); exit(EXIT_FAILURE); } // Setting socket options int opt = 1; if (setsockopt(server_fd, SOL_SOCKET, SO_REUSEADDR | SO_REUSEPORT, &opt, sizeof(opt))) { perror("setsockopt"); exit(EXIT_FAILURE); } // Binding socket to port 8080 address.sin_family = AF_INET; address.sin_addr.s_addr = INADDR_ANY; address.sin_port = htons(8080); if (bind(server_fd, (struct sockaddr *)&address, sizeof(address)) < 0) { perror("bind failed"); exit(EXIT_FAILURE); } // Listening for connections (TCP handshake happens here) if (listen(server_fd, 3) < 0) { perror("listen"); exit(EXIT_FAILURE); } // Accepting a connection (completes the handshake) if ((new_socket = accept(server_fd, (struct sockaddr *)&address, (socklen_t*)&addrlen)) < 0) { perror("accept"); exit(EXIT_FAILURE); } // Connection established, can send/receive data return 0; }Client-side Code Example
// Client-side code #include <stdio.h> #include <sys/socket.h> #include <arpa/inet.h> #include <unistd.h> #include <string.h> int main() { int sock = 0; struct sockaddr_in serv_addr; // Creating socket if ((sock = socket(AF_INET, SOCK_STREAM, 0)) < 0) { printf("n Socket creation error n"); return -1; } serv_addr.sin_family = AF_INET; serv_addr.sin_port = htons(8080); // Convert IPv4 address from text to binary if(inet_pton(AF_INET, "127.0.0.1", &serv_addr.sin_addr) =>TCP Packet Structure
TCP Header Format
0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Source Port | Destination Port | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Sequence Number | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Acknowledgment Number | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Data | |C|E|U|A|P|R|S|F| | | Offset| Res. |W|C|R|C|S|S|Y|I| Window | | | |R|E|G|K|H|T|N|N| | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Checksum | Urgent Pointer | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Options | Padding | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | data | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+Key TCP Flags for Handshake
- SYN (Synchronize): Initiates a connection
- ACK (Acknowledge): Acknowledges received data
- FIN (Finish): No more data from sender
- RST (Reset): Reset the connection
- PSH (Push): Push data to the application immediately
- URG (Urgent): Urgent data present
Handshake Packet Configuration
- SYN packet: SYN=1, ACK=0
- SYN-ACK packet: SYN=1, ACK=1
- ACK packet: SYN=0, ACK=1
Security Implications of TCP Handshake
SYN Flood Attack
A SYN flood is a form of denial-of-service attack where an attacker sends a sequence of SYN packets but never completes the handshake. This leaves connections in a half-open state and can exhaust server resources.
TCP Sequence Prediction
If an attacker can predict the sequence numbers used in TCP connections, they can potentially hijack sessions or inject data into existing connections.
TCP Reset Attack
An attacker can disrupt existing TCP connections by sending forged RST packets if they can guess or intercept valid sequence numbers.
Protection Mechanisms
- SYN cookies: A technique to prevent SYN flood attacks by avoiding resource allocation until the handshake completes
- Random Initial Sequence Numbers (ISN): Makes sequence prediction more difficult
- TCP Authentication Option (TCP-AO): Authenticates TCP segments to prevent forgery
- Firewall protection: Limiting SYN packets from a single source
-
-
AuthorPosts
- You must be logged in to reply to this topic.